|
Network
Security
Securing your
data and infrastructure is a complex task that involves human
engineering as well as hardware and software solutions. Although
TENGMAI is experienced with a wide variety of firewall and VPN
products, our initial focus includes issues of employee access,
rights and authentication.
After reviewing
the security analysis that is included with our site surveys,
TENGMAI will advise you about the human factors involved in
security. Many security breaches originate inside organizations. As
Cisco puts it: "...employees, through mischief, malice, or mistake
often manage to damage their own companies' networks. Furthermore,
remote partners and employees pose the same threats as internal
employees, as well as the risk of security breaches if their remote
networking assets are not properly secured and monitored."
Another internal
security issue involves Social Engineering where hackers get network
security information (e.g. passwords) by calling employees and
representing themselves as Help Desk personnel and simply asking the
employees what their passwords are. Other examples are bribing
employees for information or even searching offices for co- workers'
passwords.

Firewalls
Once you have determined your employee password and security
policies, it is time to consider what type of firewall to install.
Firewalls are hardware or software products that implement access
control policies between your network and the outside world.
Firewalls are designed to both block unacceptable inbound traffic
and to permit desired outbound traffic. This means that the network
administrator must determine which kinds of traffic to block and
which types should be allowed. The administrator must also make sure
that remote workers have desktop firewalls installed on their
computers so that hackers cannot access company networks by
"piggybacking" on the remote employee's session. There are two main
types of firewalls available (but keep in mind that some products
combine both types into a single "appliance"):
1. Stateful Inspection products from Cisco, Netscreen, WatchGuard,
Check Point and others work by examining packets as they enter or
leave the network. Both the IP addresses and the "context" of the
packets are examined to see if they match the permissible criteria
as configured by the network administrator. The context refers to
the context of the user session e.g. if a user accesses an FTP
server to download a file, the firewall monitors the entire process.
It blocks non-FTP activity while keeping open the FTP firewall port
until the download is complete. In this example, the firewall
monitors client to server connections and only allows responses to
permissible client requests.
2. Application Proxy firewalls like those from Network Associates,
Secure Computing Corp., WatchGuard, Symantec and others utilize
proxy applications that mediate the communications between a client
and a destination service. The proxy software protects the network
computers by hiding them from the outside world. Incoming packets
are inspected for content that violates security policies.
Executable files, Java applets, ActiveX files and other potentially
malicious code can be screened out. Proxies are usually configured
for the standard types of Internet traffic like SMTP, FTP, and HTTP.
Custom proxies can also be configured for individual applications
and services (e.g. Real Audio).
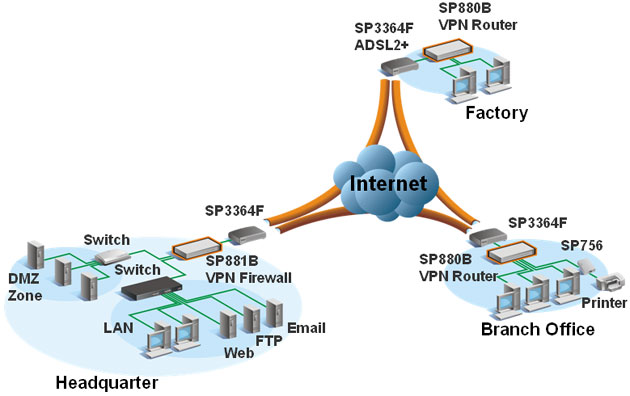
VPN's
Many firewalls also include Virtual Private Network (VPN)
capabilities to allow branch offices and telecommuters to securely
access the company network over phone lines or via the Internet.
Security is typically ensured through the use of a tunneling
protocol like IPSec and high level encryption - e.g. 168-bit 3DES.
For large
enterprises, the ASIC based firewalls offer speeds up to
2Gbits/second and capacities up to 40,000 simultaneous connections.
But for small to medium sized organizations, the all-in-one
appliance type firewalls make the most sense. They often include
VPNs and other useful features like bandwidth management, URL
content filtering (to prevent employees from visiting undesirable
sites) and Network Address Translation or NAT to hide your network
from external threats. The appliance type firewalls like those from
WatchGuard and SonicWall also simplify the task of security
configuration and management.
Anti-Virus
Products
The virus attacks of the past couple of years demonstrate the
importance of installing and maintaining anti-virus software on your
network servers and desktops. TENGMAI can assist you with products
from Symantec, McAfee and others. Many current products monitor your
entire network and feature automatic upgrades over the Internet.

|